October
6
SophosXG IPsec OpenWrt site-to-site
OpenWRT:
This post assumes that you have installed all required packages on router.
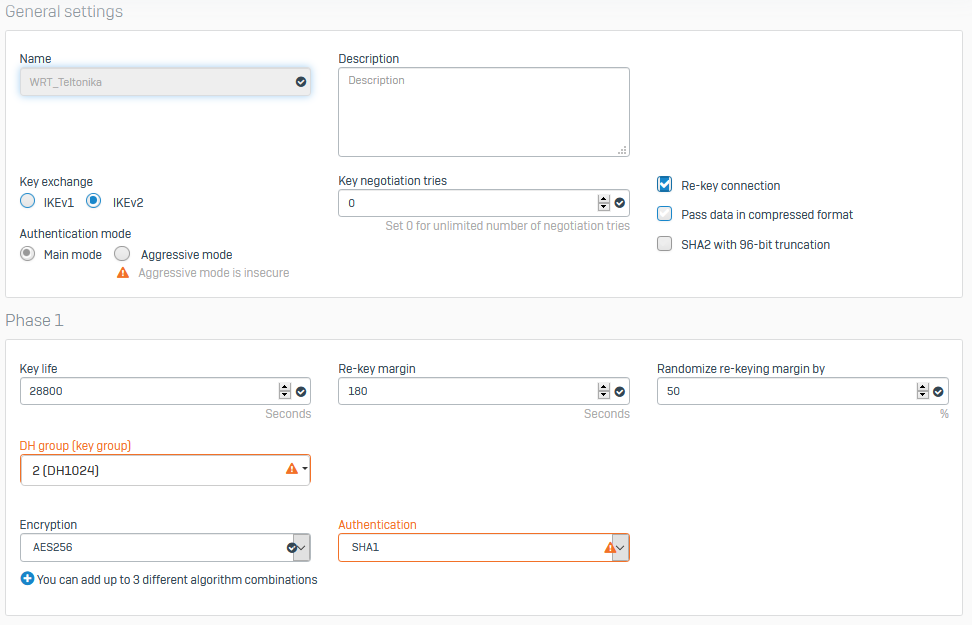
/etc/conf/ipsec.conf
config conn ‘CONNECTION_NAME’
option enabled ‘1’
option keyexchange ‘ikev2’
option ipsec_type ‘tunnel’
option auto ‘start’
option leftfirewall ‘yes’
option auth ‘psk’
option right ‘REMOTE_VPN_PUBLIC_IP’
option rightfirewall ‘yes’
# option allow_webui ‘1’
option ike_authentication_algorithm ‘sha1’
option ike_dh_group ‘modp1024’
option ikelifetime ‘28800s’
option esp_encryption_algorithm ‘aes128’
option esp_hash_algorithm ‘sha1’
option esp_pfs_group ‘modp1024’
option keylife ‘28800s’
option ike_encryption_algorithm ‘aes256’
option forceencaps ‘yes’
option my_identifier ‘LOCAL_ID’
option rightid ‘REMOTE_ID’
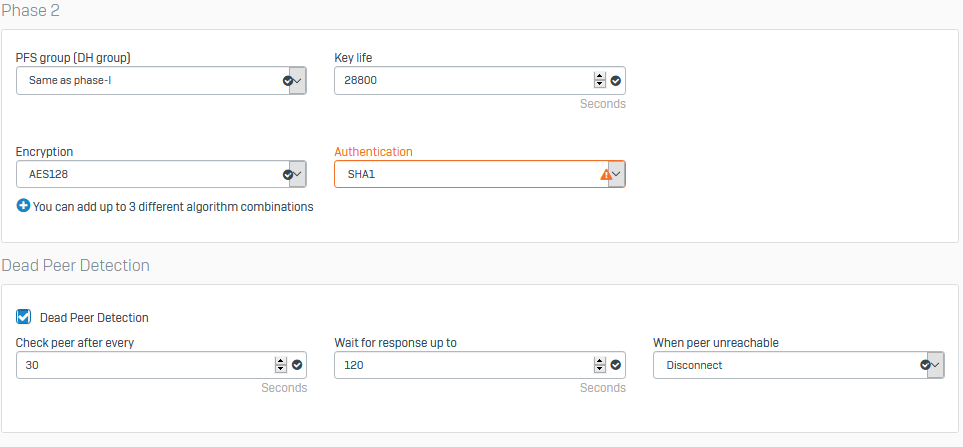
option dpdaction ‘restart’
list leftsubnet ‘LOCAL_LAN/24’
list rightsubnet ‘REMOTE_LAN/24’
# option keep_enabled ‘1’
# option ping_ipaddr ‘192.168.200.30’
# option ping_period ’15’
config preshared_keys
option psk_key ‘VERY_LONG_PSK_UP_TO_32_CHARS’
list id_selector ‘LOCAL_ID’config zone
option name ‘wan’
option input ‘REJECT’
option output ‘ACCEPT’
option forward ‘REJECT’
option masq ‘1’
option mtu_fix ‘1’
option network ‘wan wan6’
list masq_dest ‘!REMOTE_LAN/24’Enable and start IPsec
/etc/init.d/ipsec enable
/etc/init.d/ipsec startSophos XG
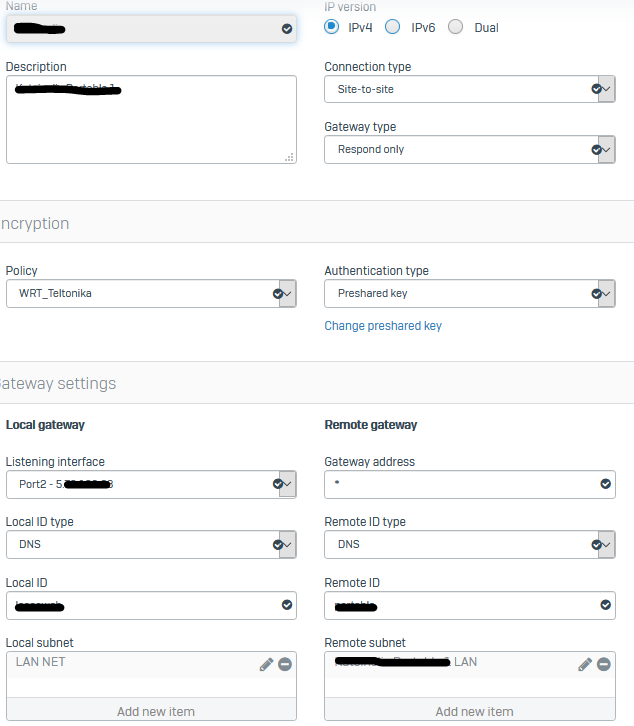
IPsec Policy (low security for low end devices)